Cluster API and Kubernetes version support
- Cluster API and Kubernetes version support
Version support policies
Cluster API release support
This paragraph documents the general rules defining how we determine Cluster API supported releases.
A Cluster API release correspond to a release in the GitHub repository for this project, and the corresponding images published in the Kubernetes docker registry.
For the sake of this document, the most important artifacts included in a Cluster API release are:
- The Cluster API Core provider image
- The Kubeadm Bootstrap provider image
- The Kubeadm Control Plane provider image
- The clusterctl binary
The Cluster API team will release a new Cluster API version approximately every four months (three releases each year). See release cycle and release calendars for more details about Cluster API releases management.
The Cluster API team actively supports the latest two minor releases (N, N-1); support in this context means that we:
- Have CI signal with E2E tests, unit tests, CVE scans etc.
- Accept bug fixes, perform golang or dependency bumps, etc.
- Periodically cut patch releases
On top of supporting the N and N-1 releases, the Cluster API team also maintains CI signal for the Cluster API N-2 releases in case we have to do an emergency patch release.
- If there is a need for an emergency patch, e.g. to fix a critical security issue, please bring this up to maintainers and it will be considered on a case-by-case basis.
All considered, each Cluster API minor release is supported for a period of roughly 12 months:
- The first eight months of this timeframe will be considered the standard support period for a minor release.
- The next four months the minor release will be considered in maintenance mode.
- At the end of the four-month maintenance mode period, the minor release will be considered EOL (end of life) and cherry picks to the associated branch are to be closed soon afterwards.
The table below documents support matrix for Cluster API versions (versions older than v1.0 omitted).
| Minor Release | Status | Supported Until (including maintenance mode) |
|---|---|---|
| v1.13.x | Standard support period | in maintenance mode when v1.15.0 will be released, EOL when v1.16.0 will be released |
| v1.12.x | Standard support period | in maintenance mode when v1.14.0 will be released, EOL when v1.15.0 will be released |
| v1.11.x | Maintenance mode | Maintenance mode since 2026-04-21 - v1.13.0 release date, EOL when v1.14.0 will be released |
| v1.10.x | EOL | EOL since 2026-04-21 - v1.13.0 release date |
| v1.9.x | EOL | EOL since 2025-12-18 - v1.12.0 release date |
| v1.8.x | EOL | EOL since 2025-08-12 - v1.11.0 release date |
| v1.7.x | EOL | EOL since 2025-04-22 - v1.10.0 release date |
| v1.6.x | EOL | EOL since 2024-12-10 - v1.9.0 release date |
| v1.5.x | EOL | EOL since 2024-08-12 - v1.8.0 release date |
| v1.4.x | EOL | EOL since 2024-04-16 - v1.7.0 release date |
| v1.3.x | EOL | EOL since 2023-12-05 - v1.6.0 release date |
| v1.2.x | EOL | EOL since 2023-07-25 - v1.5.0 release date |
| v1.1.x | EOL | EOL since 2023-03-28 - v1.4.0 release date |
| v1.0.x | EOL | EOL since 2022-12-01 - v1.3.0 release date |
Skip upgrades
Cluster API supports at maximum n-3 minor version skip upgrades.
For example, if you are running Cluster API v1.6.x, you can upgrade up to Cluster API v1.9.x skipping intermediate minor versions (v1.6 is v1.9 minus three minor versions).
Downgrades
Cluster API does not support version downgrades.
Cluster API release vs API versions
Each Cluster API release can support one or more API versions.
An API version is determined from the GroupVersion defined in the top-level api/ package of a specific Cluster API release, and it is used
in the apiVersion field of Cluster API custom resources.
An API version is considered deprecated when a new API version is published.
API deprecation and removal follow the Kubernetes Deprecation Policy; Cluster API maintainers might decide to support API versions longer than what is defined in the Kubernetes policy.
| API Version | Status | Supported Until |
|---|---|---|
| v1beta2 | Supported | at least 9 months or 3 minor releases after a newer API version will be released |
| v1beta1 | Deprecated | Deprecated since CAPI v1.11; in v1.16, April 2027 v1beta1 will stop to be served |
See 11920 for details about the v1beta1 removal plan.
Cluster API release vs contract versions
Each Cluster API contract version defines a set of rules a provider is expected to comply with to interact with a specific Cluster API release. Those rules can be in the form of CustomResourceDefinition (CRD) fields and/or expected behaviors to be implemented. See provider contracts
Each Cluster API release supports one contract version, and by convention the supported contract version matches the newest API version in the same Cluster API release.
A contract version might be temporarily compatible with older contract versions to ease the transition of providers to a new supported version; compatibility for older contract versions will be dropped when the older contract version is EOL.
| Contract Version | Compatible with contract versions | Status | Supported Until |
|---|---|---|---|
| v1beta2 | v1beta1 (temporarily) | Supported | After a newer API contract will be released |
| v1beta1 | Deprecated | Deprecated since CAPI v1.11; in v1.16, April 2027 compatibility with the v1beta1 contract will be considered EOL |
See 11920 for details about the v1beta1 removal plan.
Supported Cluster API - Cluster API provider version Skew
When running a Cluster API release, all the provider installed in the same management cluster MUST implement the CustomResourceDefinition (CRD) fields and/or expected behaviors defined by the release’s contract version.
As a corollary, provider’s version number and provider’s API version number are not required to match Cluster API versions.
Kubernetes versions support
This paragraph documents the general rules defining how the Cluster API team determines supported Kubernetes versions for every Cluster API release.
When a new Cluster API release is cut, we will document the Kubernetes version compatibility matrix the release has been tested with in the table below.
Each Cluster API minor release supports (when it’s initially created):
- Four Kubernetes minor releases for the management cluster (N - N-3)
- Six Kubernetes minor releases for the workload cluster (N - N-5)
When a new Kubernetes minor release is available, the Cluster API team will try to support it in upcoming Cluster API patch releases, thus:
- extending the support matrix for the latest supported Cluster API minor release to:
- Five Kubernetes minor releases for the management cluster (N - N-4)
- Seven Kubernetes minor releases for the workload cluster (N - N-6)
- extending the support matrix for the Cluster API minor release before that to: (this will be only done for Kubernetes >= v1.36)
- Six Kubernetes minor releases for the management cluster (N - N-5)
- Eight Kubernetes minor releases for the workload cluster (N - N-7)
Please note that we will try to support the new Kubernetes release, there is no guarantee that we will be able to backport the required changes as they might be breaking.
Example:
- When Cluster API v1.7.0 is released it will support:
- v1.26.x to v1.29.x for the management cluster
- v1.24.x to v1.29.x for the workload cluster
- When Kubernetes 1.30 is released: v1.7.x will support:
- v1.26.x to v1.30.x for the management cluster
- v1.24.x to v1.30.x for the workload cluster
- When Kubernetes 1.31 is released: v1.7.x will support:
- v1.26.x to v1.31.x for the management cluster
- v1.24.x to v1.31.x for the workload cluster
See Kubernetes version Support and Cluster API deployment model to understand how the way you deploy Cluster API might affect the Kubernetes version support matrix for a Cluster.
On a final comment, let’s praise all the contributors keeping care of such a wide support matrix. If someone is looking for opportunities to help with the project, this is definitely an area where additional hands and eyes will be more than welcome and greatly beneficial to the entire community.
Maximum version skew between various Kubernetes components
Standard Kubernetes version Skew Policy defines the maximum version skew supported between various Kubernetes components within a single cluster.
Notably, version skew between various Kubernetes components also define constraints to be observed by Cluster API, Cluster API providers or Cluster API users when performing Kubernetes version upgrades.
In some cases, also Cluster API and/or Cluster API providers are defining additional version skew constraints. For instance:
- If you are using kubeadm as a bootstrapper, you must abide to the kubeadm skew policy.
- If you are using image builder, all the Kubernetes components on a single machine are of the same version
- If your Cluster has a defined topology, with
Cluster.spec.topologyset and referencing a ClusterClass, Cluster API enforces a single Kubernetes version for all the machines in the cluster.
Supported versions matrix by provider or component
Core provider (cluster-api-controller)
The following table defines the support matrix for the Cluster API core provider. See Cluster API release support and Kubernetes versions support.
| v1.11, Maintenance Mode | v1.12 | v1.13 | |
|---|---|---|---|
| Kubernetes v1.28 | ✓ (only workload) | ||
| Kubernetes v1.29 | ✓ (only workload) | ✓ (only workload) | |
| Kubernetes v1.30 | ✓ | ✓ (only workload) | ✓ (only workload) |
| Kubernetes v1.31 | ✓ | ✓ | ✓ (only workload) |
| Kubernetes v1.32 | ✓ | ✓ | ✓ |
| Kubernetes v1.33 | ✓ | ✓ | ✓ |
| Kubernetes v1.34 | ✓ >= v1.11.1 | ✓ | ✓ |
| Kubernetes v1.35 | ✓ >= v1.12.1 | ✓ |
See also Kubernetes version specific notes.
Kubeadm Bootstrap provider (kubeadm-bootstrap-controller)
For each version of the Cluster API core provider, there is a corresponding version of the Kubeadm Bootstrap provider.
The Kubeadm Bootstrap provider also follows the same support rules defined in Cluster API release support and Kubernetes versions support.
As a consequence, the support matrix for the Kubeadm Bootstrap provider is the same as the one defined for the Cluster API Core provider.
Kubeadm configuration API Support
When creating new machines, the Kubeadm Bootstrap provider generates kubeadm init/join configuration files using the kubeadm API version recommended for the target Kubernetes version.
| kubeadm API Version | |
|---|---|
| Kubernetes v1.27 | v1beta3 |
| Kubernetes v1.28 | v1beta3 |
| Kubernetes v1.29 | v1beta3 |
| Kubernetes v1.30 | v1beta3 |
| Kubernetes v1.31 | v1beta4 |
| Kubernetes v1.32 | v1beta4 |
| Kubernetes v1.33 | v1beta4 |
| Kubernetes v1.34 | v1beta4 |
| Kubernetes v1.35 | v1beta4 |
Kubeadm Control Plane provider (kubeadm-control-plane-controller)
For each version of the Cluster API core provider, there is a corresponding version of the Kubeadm Control Plane provider.
The Kubeadm Control Plane provider also follows the same support rules defined in Cluster API release support and Kubernetes versions support.
As a consequence, the support matrix for the Kubeadm Control Plane provider is the same as the one defined for the Cluster API Core provider.
Bootstrap provider Support
The Kubeadm Control Plane requires the Kubeadm Bootstrap provider of the same version.
Etcd API Support
The Kubeadm Control Plane provider communicates with the API server and etcd members of every Workload Cluster whose control plane it owns. All the Cluster API Kubeadm Control Plane providers currently supported are using etcd v3 API when communicating with etcd.
CoreDNS Support
Each version of the Kubeadm Control Plane can upgrade up to a max CoreDNS version. Notably, the Max CoreDNS version could change also with patch releases.
| KCP Version | Max CoreDNS Version |
|---|---|
| v1.5 | v1.10.1 |
| >= v1.5.1 | v1.11.1 |
| v1.6 | v1.11.1 |
| v1.7 | v1.11.1 |
| v1.8 | v1.11.3 |
| >= v1.8.9 | v1.12.0 |
| >= v1.8.12 | v1.12.1 |
| v1.9 | v1.11.3 |
| >= v1.9.4 | v1.12.0 |
| >= v1.9.7 | v1.12.1 |
| >= v1.9.11 | v1.12.3 |
| v1.10 | v1.12.1 |
| >= v1.10.5 | v1.12.3 |
| v1.10.7 | v1.12.4 |
| >= v1.10.8 | v1.13.1 |
| v1.11 | v1.12.3 |
| v1.11.2 | v1.12.4 |
| >= v1.11.3 | v1.13.1 |
| >= v1.11.6 | v1.14.1 |
| v1.12 | v1.13.1 |
| >= v1.12.3 | v1.14.1 |
Other providers
Cluster API has a vibrant ecosystem of awesome providers maintained by independent teams and hosted outside of the Cluster API GitHub repository.
To understand the list of supported versions for a specific provider, its own Kubernetes support matrix, supported API versions, supported contract version and specific skip upgrade rules, please see its documentation. Please refer to providers list
In general, if a provider version M says it is compatible with Cluster API version N, then it MUST be compatible with a subset of the Kubernetes versions supported by Cluster API version N.
clusterctl
It is strongly recommended to always use the latest patch version of clusterctl to get all the fixes/latest changes.
In case of upgrades, clusterctl should be upgraded first and then used to upgrade all the other components.
Annexes
Kubernetes version Support and Cluster API deployment model
The most common deployment model for Cluster API assumes all providers are running on the Management Cluster and managing the lifecycle of a set of separate Workload clusters.
“All providers” includes: the core provider, a Bootstrap provider, a Control Plane provider (optional), and at least one infrastructure provider.
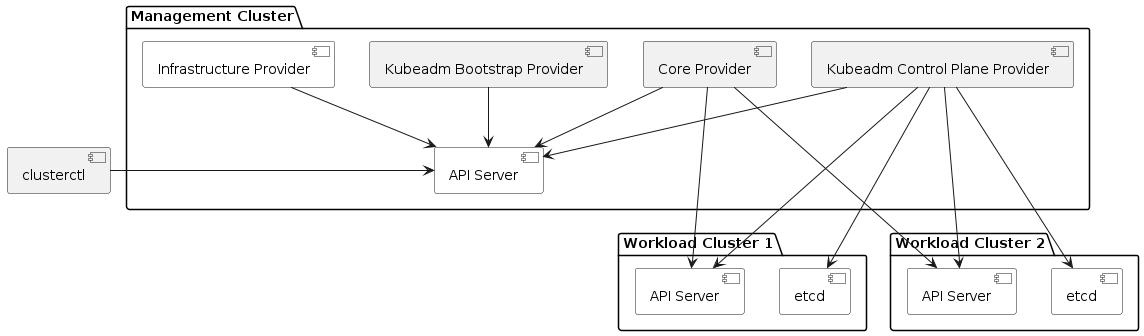
In this scenario, the Kubernetes version of the Management and Workload Clusters are allowed to be different. Additionally, Management Clusters and Workload Clusters can be upgraded independently and in any order.
In another deployment model for Cluster API, the Cluster API providers are used not only to manage the lifecycle of separate Workload clusters, but also to manage the lifecycle of the Management cluster itself. This cluster is also referred to as a “self-hosted” cluster.
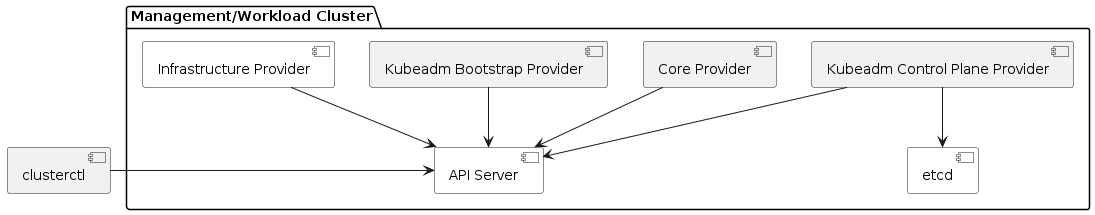
The Kubernetes version of the “self-hosted” cluster is limited to the Kubernetes version currently supported for the Management clusters.
Kubernetes version specific notes
1.36:
- Kubeadm Bootstrap provider:
- The
ControlPlaneKubeletLocalModefeature gate graduated to GA and has been removed in Kubernetes v1.36. CAPI will no longer set this feature gate explicitly for Kubernetes 1.36+. For Kubernetes versions 1.31-1.35, CAPI continues to set it automatically to ensure kubelet continues working during control plane upgrades.
- The
1.31:
- All providers:
- It is not possible anymore to continuously apply CRDs that are setting
caBundleto an invalid value (in our caseCg==). Instead of setting a dummy value thecaBundlefield should be dropped (#10972).
- It is not possible anymore to continuously apply CRDs that are setting
- Kubeadm Bootstrap provider:
1.29:
- In-tree cloud providers are now switched off by default. Please use DisableCloudProviders and DisableKubeletCloudCredentialProvider feature flags if you still need this functionality. (https://github.com/kubernetes/kubernetes/pull/117503)